Disrupted Trust, How Scattered Lapsus$ Hunters Breached Betterment and Turned Customer Data Into a Weapon
In early January 2026, one of the largest automated investment platforms in the United States found itself exposed not by a software flaw or a zero-day exploit, but by a far more familiar weakness...
In early January 2026, one of the largest automated investment platforms in the United States found itself exposed not by a software flaw or a zero-day exploit, but by a far more familiar weakness, trust. Betterment suffered a data breach that exposed sensitive customer information after attackers abused a trusted third-party platform, rapidly converting stolen access into a large-scale crypto scam.
This incident was not accidental, opportunistic, or novel. It was the deliberate work of Scattered Lapsus$ Hunters, a cybercriminal ecosystem that has refined identity abuse into a repeatable intrusion model. The breach highlights a growing reality for fintech and beyond, attackers no longer need to break systems when they can convincingly impersonate them.
A Quiet Breach With Loud Consequences
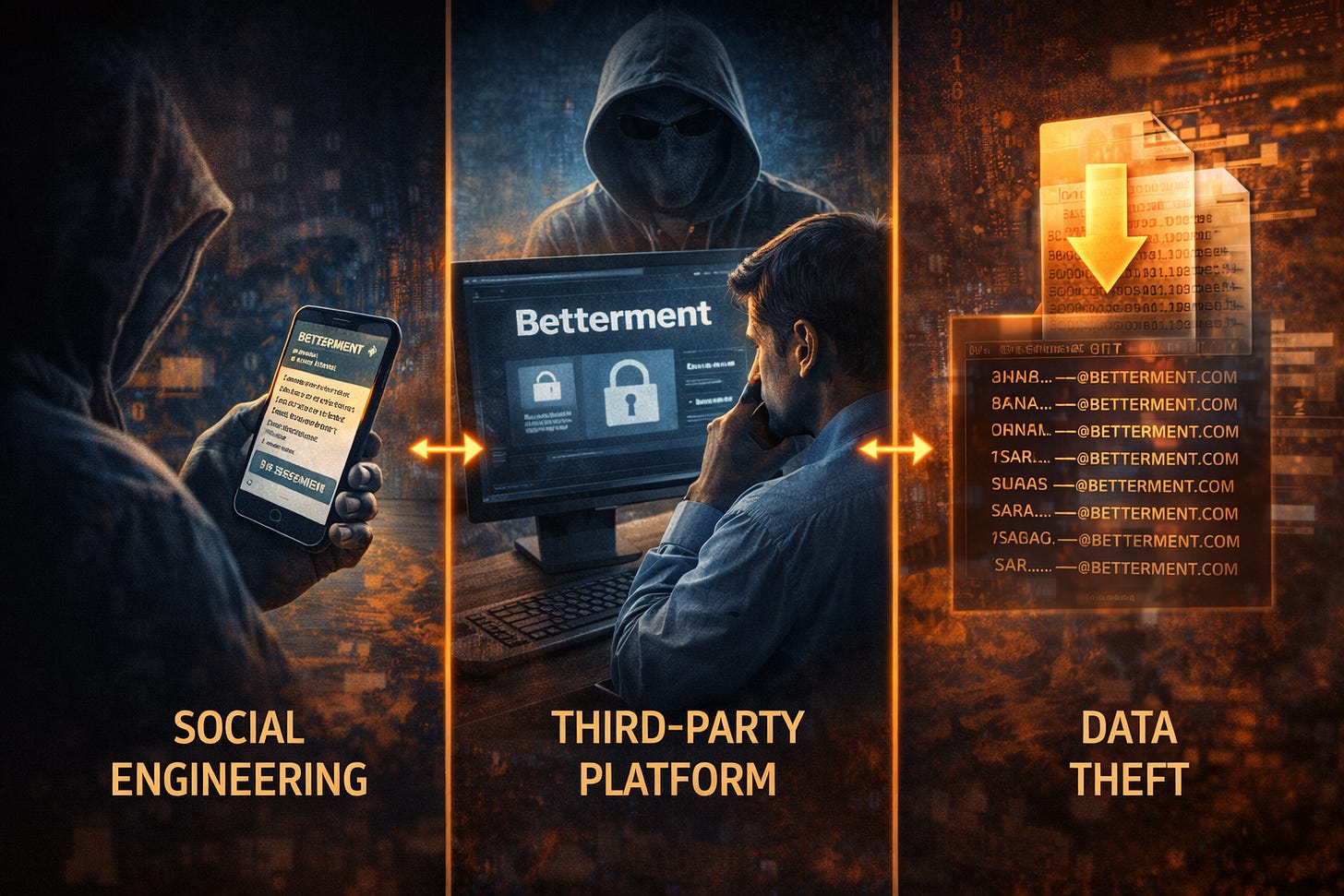
On January 9, attackers gained access to third-party software used by Betterment for customer communications through social engineering. Rather than targeting core financial systems, the operation focused on exploiting the implicit trust embedded in outsourced platforms, a tactic increasingly favored by modern threat actors.
Once access was secured, fraudulent messages were sent to Betterment customers, disguised as legitimate company notifications. The messages promoted a classic crypto giveaway scam, promising to triple cryptocurrency deposits sent to attacker-controlled wallets. Because the messages originated from a trusted communication channel, the scam carried a level of legitimacy that would have been difficult for many recipients to immediately question.
Betterment quickly disabled the compromised access and warned customers through official channels. The company stated that no passwords, Social Security numbers, or investment accounts were directly accessed. However, the damage had already been done.
The Data That Slipped Through the Cracks
The attackers exfiltrated personally identifiable information, including:
Full names
Email addresses
Physical addresses
Phone numbers
Dates of birth
Subsequent analysis indicated that more than 1.4 million unique customer records were exposed. While this data does not enable immediate account takeover, its value lies elsewhere. Aggregated PII fuels identity fraud, targeted phishing, SIM swapping, and high-confidence impersonation campaigns.
This reflects a broader shift in attacker priorities. Instead of going after transactional control, adversaries increasingly harvest data that enables scalable deception. The financial impact may not be immediate, but the downstream risk persists long after breach notifications fade.
Anatomy of the Attack, Identity Over Exploitation
This intrusion did not rely on advanced malware, zero-days, or persistence mechanisms.
No core banking systems were compromised
No vulnerabilities were publicly disclosed
Access was gained through deception, not exploitation
A third-party SaaS platform became the entry point, demonstrating how communication and marketing systems now function as trust delivery mechanisms, not peripheral tools. Once compromised, they allow attackers to speak with the full authority of the brand.
This model bypasses many traditional security controls. MFA, EDR, and network segmentation offer limited protection when an attacker successfully convinces a system, or a human, that they belong.
Attribution, Scattered Lapsus$ Hunters Behind the Breach
The Betterment breach was carried out by Scattered Lapsus$ Hunters, a federated cybercriminal brand that has emerged as one of the most disruptive forces in recent years.
Scattered Lapsus$ Hunters is not a single hierarchical group. It is a loosely connected ecosystem of operators that consolidated reputational and operational elements from Scattered Spider, ShinyHunters, and LAPSUS$. Rather than merging infrastructure, the cluster operates as a shared brand, amplifying visibility, credibility, and intimidation across campaigns.
This federated model allows multiple actors to collaborate, imitate, or operate independently while benefiting from a common identity. The result is a threat actor that behaves less like a gang and more like a franchise.
A Brand Built on Identity Abuse and Visibility
According to threat intelligence reporting, Scattered Lapsus$ Hunters prioritizes social engineering and trust exploitation over technical sophistication. Their operations consistently feature:
Impersonation of internal IT staff, vendors, or partners
Social engineering of employees and third parties
Abuse of SaaS platforms and identity workflows
Rapid data exfiltration followed by immediate monetization or extortion
Unlike traditional ransomware groups, Scattered Lapsus$ Hunters favors speed and impact over stealth. Access is obtained, leveraged, and discarded quickly. Data is weaponized immediately, either for extortion, resale, or follow-on fraud.
The Betterment operation fits this pattern precisely. Stolen access was used within hours. Data was repurposed for scam delivery rather than long-term persistence. The objective was not infrastructure control, but trust hijacking at scale.
Strategic Implications for Fintech
The breach underscores several uncomfortable truths for financial platforms:
Third-party platforms expand the attack surface. Any system that communicates with customers inherits brand authority, and therefore risk.
PII is now a primary objective. Data that enables impersonation is more scalable than direct theft.
Attribution models are changing. Federated threat brands blur traditional group boundaries, complicating defense and response.
Regulatory scrutiny around third-party risk, data protection, and disclosure is likely to intensify as incidents like this continue.