Google's Tensor Secrets Were in Tehran: The Insider Threat That Slipped Past Silicon Valley
Three engineers. Hundreds of files. One family scheme. And trade secrets about Google's most sensitive chip technology — photographed and carried to Iran.
The insider threat that cybersecurity teams train for just became real — and the target was one of the most guarded pieces of technology in consumer electronics: Google’s Tensor processor, the custom silicon inside every Pixel phone.
The U.S. Department of Justice has indicted three people — two sisters who worked at Google and the husband of one of them — for an alleged scheme to systematically steal trade secrets from Google and at least two other major tech companies, and transfer them to unauthorized locations, including Iran.
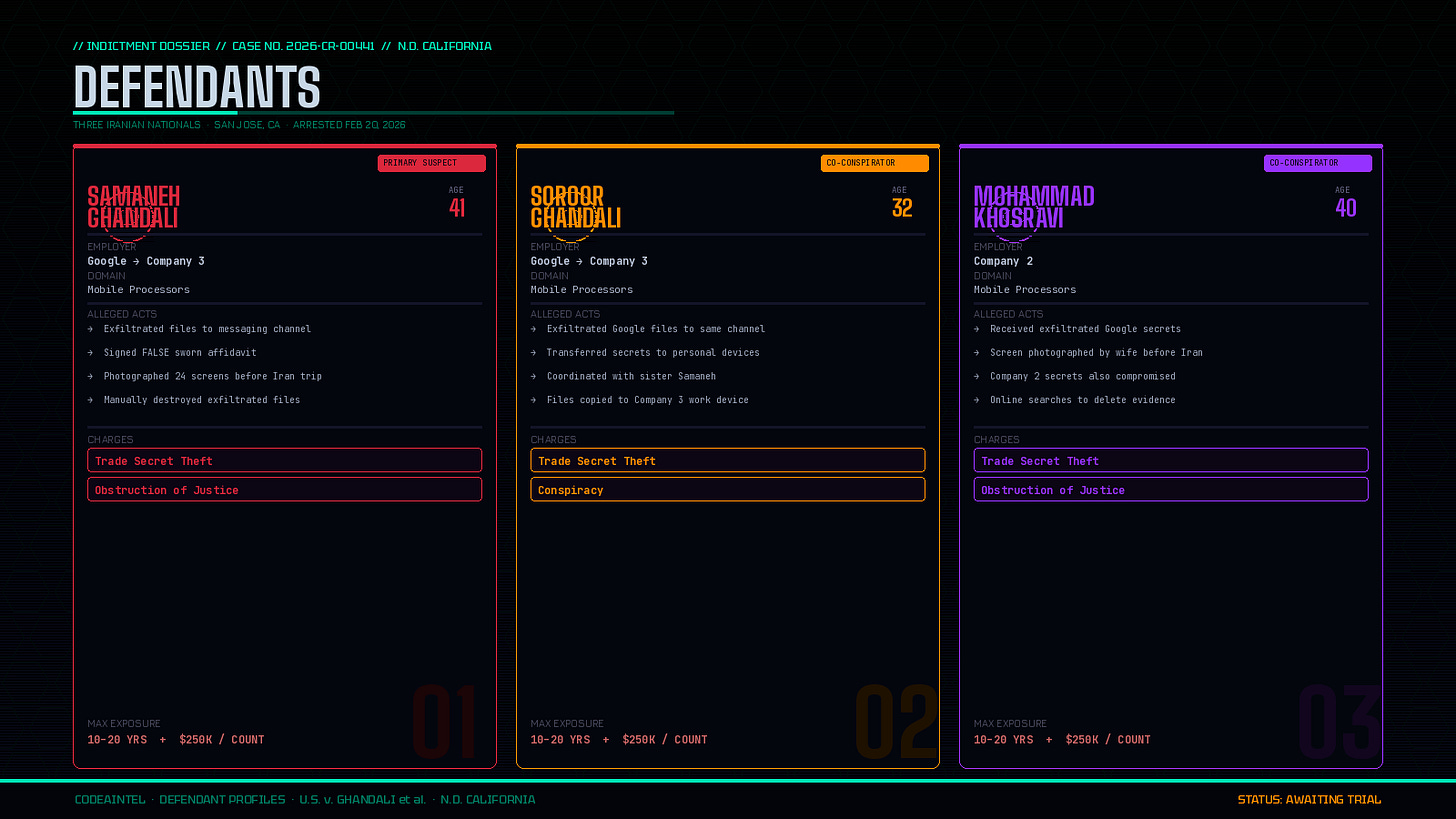
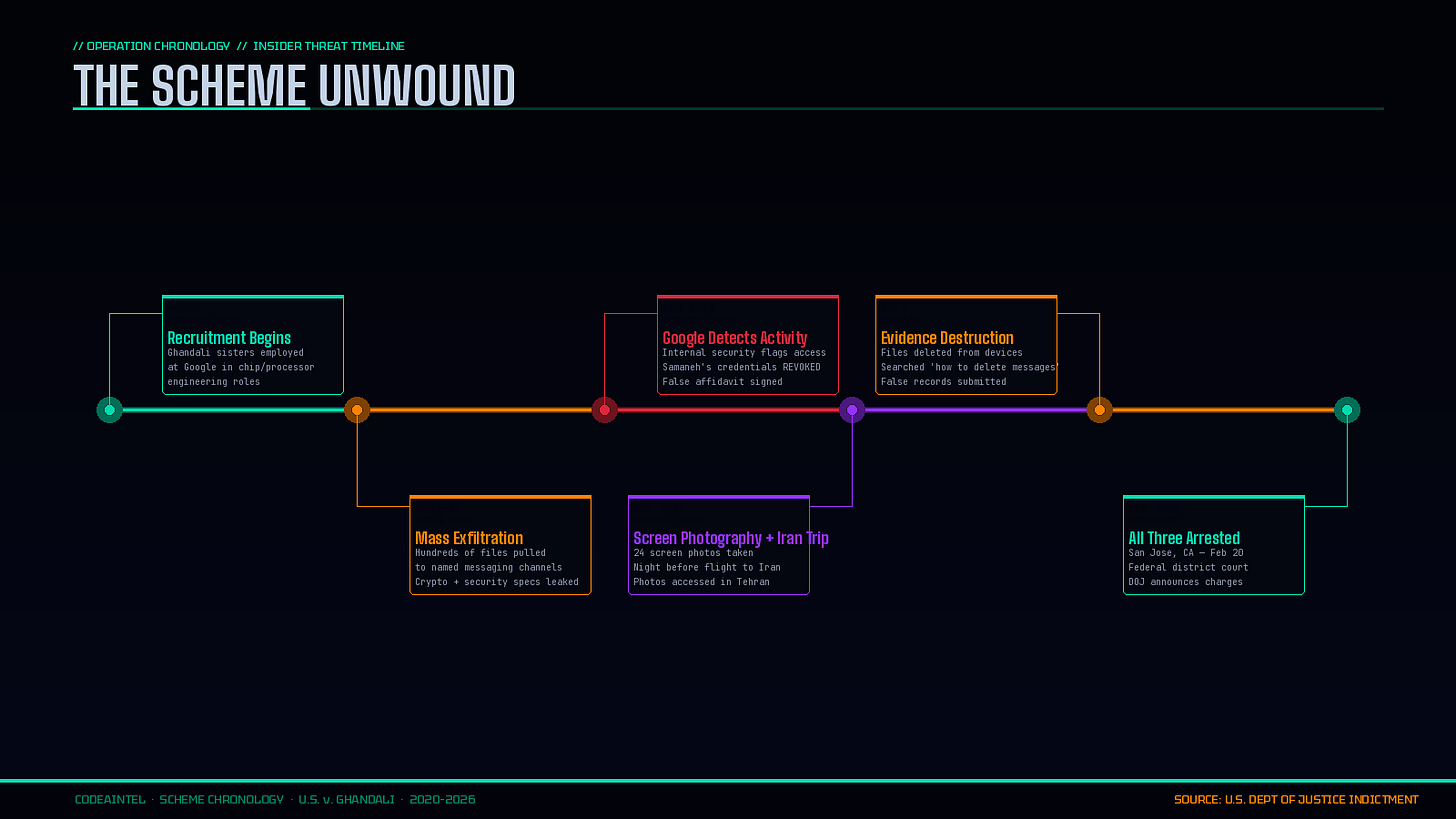
The defendants: Samaneh Ghandali, 41, a former Google engineer; her husband Mohammadjavad Khosravi, 40; and her sister Soroor Ghandali, 32, also a former Google engineer. All three are Iranian nationals who were living in San Jose. All three were arrested on Thursday and appeared in federal district court the same day.
The Anatomy of the Scheme
This wasn’t a sophisticated cyberattack from the outside. It was patient, methodical betrayal from the inside — and the operational security the defendants used makes it more alarming, not less.
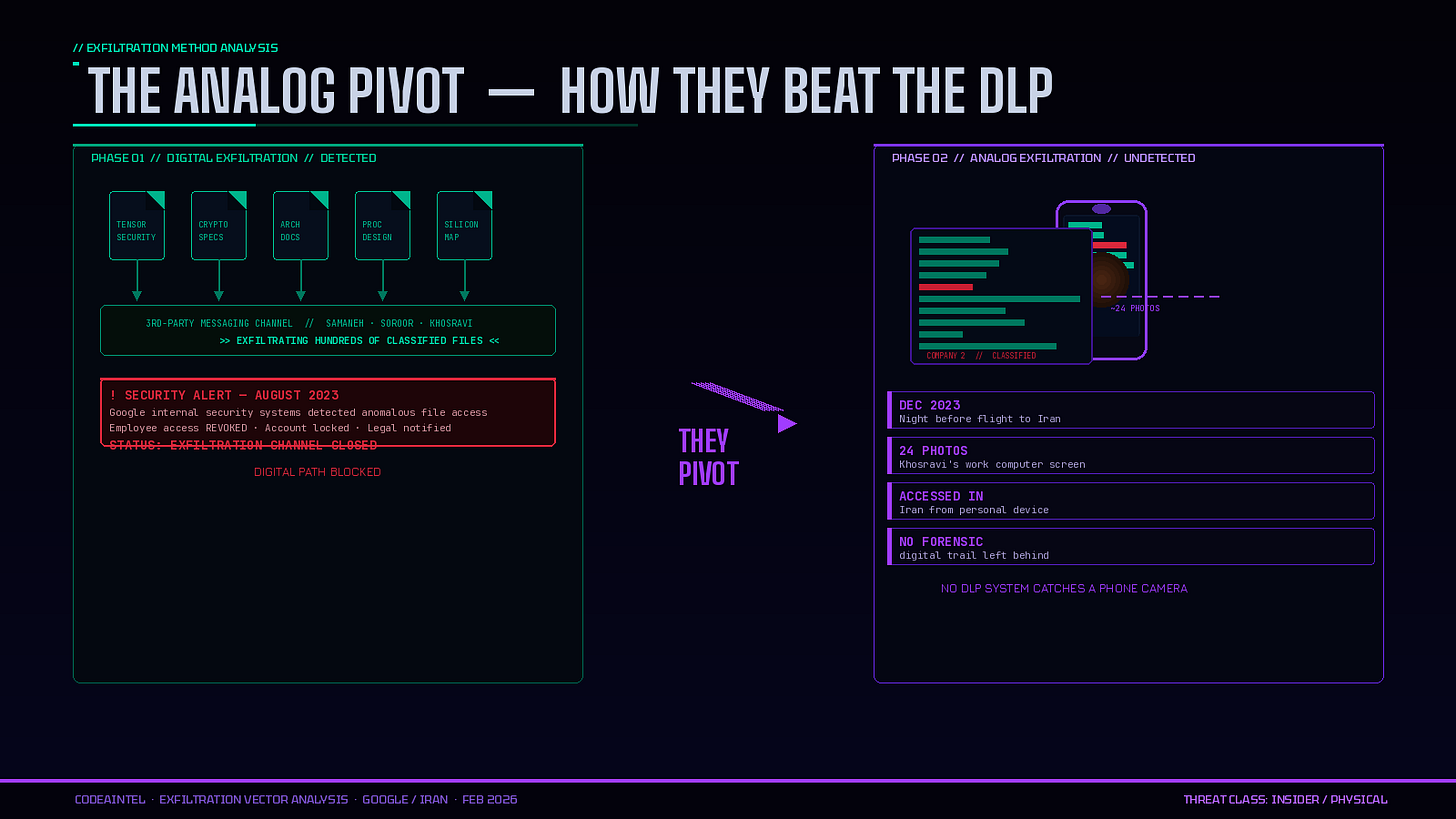
The exfiltration method: Both sisters used their legitimate employee access at Google to pull hundreds of files — including trade secrets related to processor security, cryptography, and chip architecture — and transferred them to a third-party communications platform. The channels they used were named after each defendant’s first name.
The cover-up: When Google’s internal security systems flagged Samaneh Ghandali’s activity in August 2023 and revoked her access, she signed a sworn affidavit claiming she had never shared Google’s confidential information with anyone outside the company. She had.
The analogue workaround: After digital channels were closed off, the defendants pivoted. Rather than electronically transferring files — which would leave a clear forensic trail — they manually photographed computer screens containing trade secret documents with their phones. The night before the couple traveled to Iran in December 2023, Samaneh allegedly photographed approximately 24 screens of her husband’s work computer, which contained trade secrets from his employer. Those photographs were later accessed from a device associated with her — in Iran.
The cleanup attempt: The defendants searched online for how to delete communications and how long cellular providers retain messages. They then destroyed exfiltrated files from their electronic devices.
Why This Case Matters Beyond the Headlines
The Ghandali case doesn’t exist in isolation. Less than a month ago, former Google engineer Linwei Ding was convicted for stealing thousands of Google’s confidential AI documents to build a startup in China. Now this.
Two separate insider theft cases. Two different nation-state destinations. Both targeting Google’s most strategically sensitive technologies.
The pattern forces a hard question: If Google — with its world-class security team, internal monitoring systems, and vast resources — can have trade secrets photographed off a screen and walked to Iran, what does that mean for everyone else?
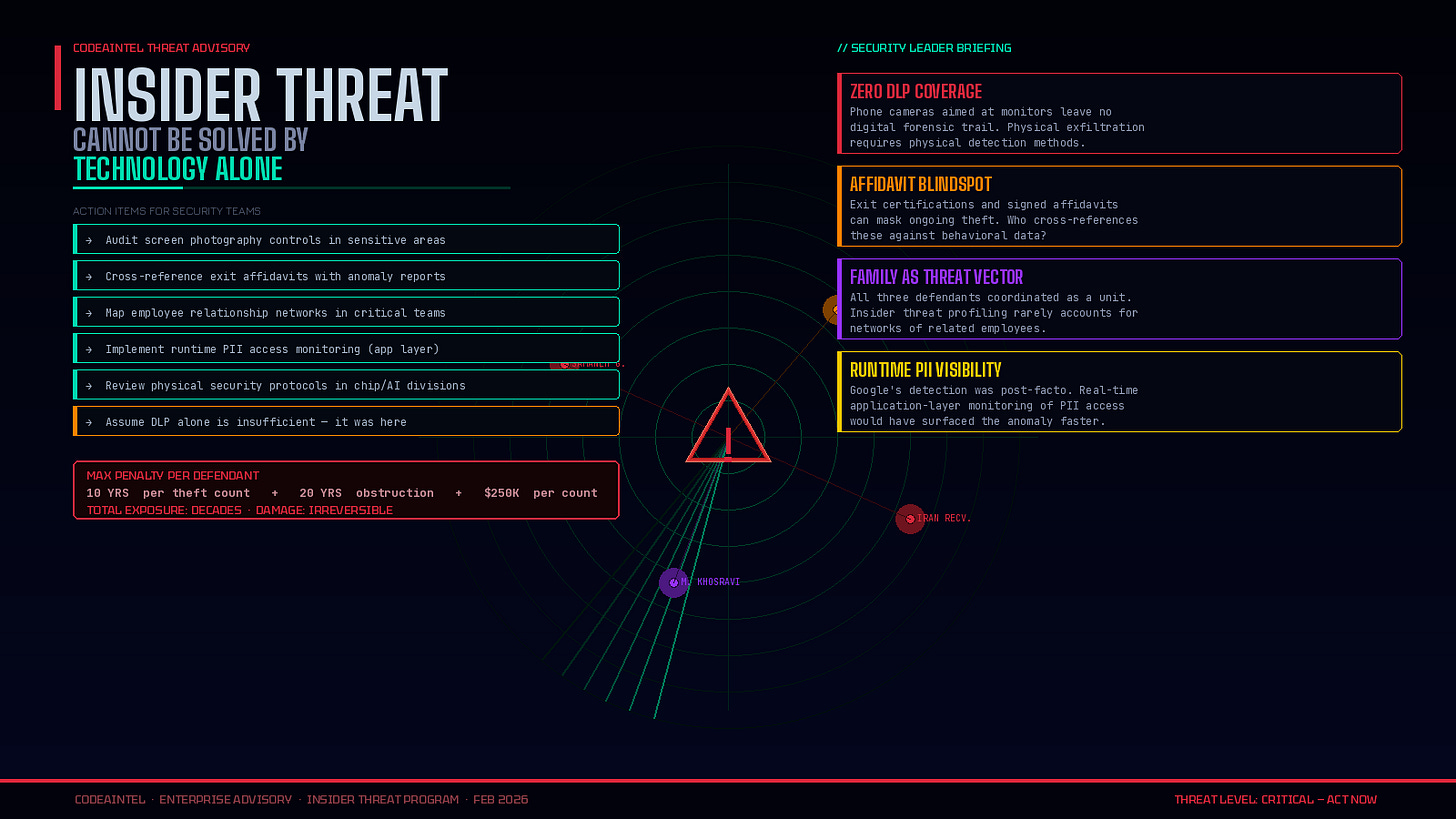
The answer is uncomfortable. Google’s systems did detect Samaneh Ghandali’s digital exfiltration. What they couldn’t fully prevent was the human workaround — the pivot to photographing screens, the signed false affidavit, the physical transport. No DLP system catches a phone camera aimed at a monitor.
The Charges and What’s at Stake
Each defendant faces up to 10 years per count of trade secret theft and up to 20 years for the obstruction of justice charge, plus a $250,000 fine per count.
The trade secrets at the center of this case — Tensor processor security architecture and cryptographic implementations — are not abstract intellectual property. They are the technical foundation of how Google secures its hardware at the silicon level. In the wrong hands, that knowledge could inform attacks on Pixel devices at scale, or accelerate a foreign nation’s semiconductor development program.
CodeAIntel Insight: The analog pivot is the most chilling detail in this indictment. These defendants got caught digitally — and responded by picking up a phone and photographing screens. That is a threat vector that lives entirely outside the reach of most enterprise DLP, CASB, and endpoint monitoring tools. The lesson for security leaders: insider threat programs can’t stop at the network edge. Physical data exfiltration — cameras, printed documents, verbal disclosure — requires a different detection model entirely. The fact that a signed false affidavit almost worked as a cover story suggests the human element of your insider threat program matters as much as the technical one. Who is reviewing those exit certifications? Who is cross-referencing them against behavioral anomalies?
Sources:
https://www.courtlistener.com/docket/72303995/united-states-v-ghandali-etal/