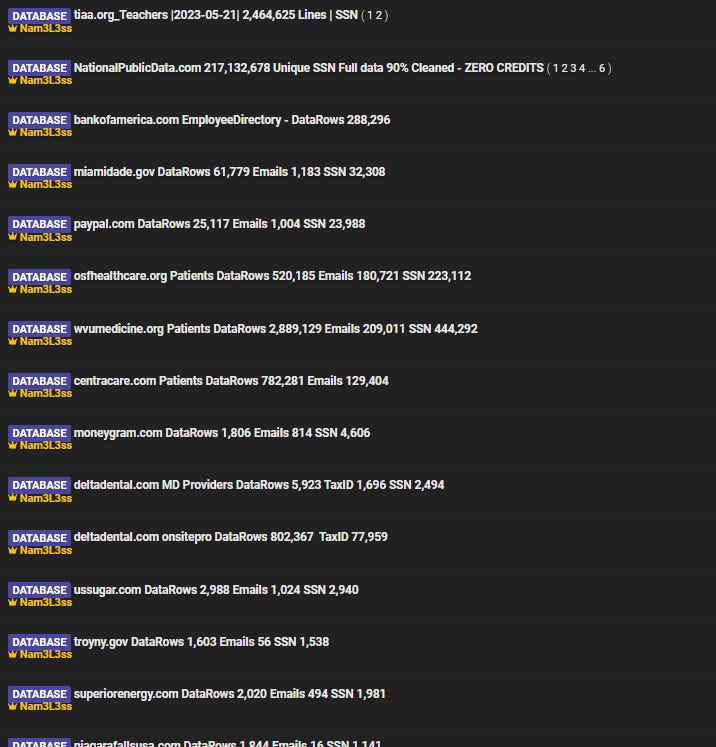
Nam3L3ss Drops Corporate Data Like It's Hot
Let's dive into this digital drama that's got corporate IT teams reaching for their stress balls.
The 2023 MOVEit breach is the gift that keeps on giving (though nobody asked for these presents), with our mysterious new player "Nam3L3ss" dropping employee data like he's sharing holiday cards.
The Breach That Keeps On Breaching Back in May 2023, Cl0p (you know, the ransomware gang that never seems to take a vacation) found a juicy vulnerability in MOVEit's file transfer software. Fast forward a few months, and enter Nam3L3ss, turning cybercrime forums into his personal LinkedIn data dump.
Just How Bad Is It? (Spoiler: Pretty Bad)
Amazon: 2.8 million employee records are out there. We're talking full names, job titles, and enough org charts to make an HR director cry.
HSBC and HP: Also got hit, though they're being shy about the numbers. (When companies don't share numbers, it's rarely because the numbers are small...)
Who Is This Nam3L3ss Character? Picture this: someone who hangs out on ransomware sites, yoinks their data, and then drops it publicly while claiming he's not in it for the money. Either we've got a cyber Robin Hood on our hands, or someone's playing 4D chess with everyone's data.
He's got a blog where he spills the tea on his activities - think of it as a hacker's Tumblr, but with more stolen databases and less fan fiction. He's apparently not a fan of ransomware groups, which is like saying you don't like your competitors in the most dramatic way possible.
The "Oh Snap" Implications This leak is basically a phisher's dream come true:
Phishing Attacks: Scammers are probably already crafting emails that look legit enough to make your security training cry
Identity Theft: Because apparently, stealing someone's identity wasn't easy enough already
Corporate Espionage: Org charts and employee data? That's like handing out your company's blueprint to everyone with an internet connection
What The Suits Are Saying Amazon's response is basically "We're fine, everything's fine" (narrator: not everything was fine). Though they did clarify that the super sensitive stuff like SSNs didn't get nabbed, so... silver linings?
What Now? If you're an org that got hit, time to:
Patch Like Your Job Depends On It: Because it probably does
Train Those Employees: Yes, even Bob from accounting who still thinks "password123" is secure
Watch Those Accounts: Like a hawk. A very paranoid hawk.
The Bottom Line The MOVEit breach is the cybersecurity equivalent of that party guest who just won't leave. And Nam3L3ss? He's the uninvited plus-one who showed up with screenshots of everyone's embarrassing photos.
Keep your patches updated, your employees trained, and maybe consider going back to sending messages by carrier pigeon. (Just kidding about the pigeon part... mostly.)