PayPal’s Silent Six Months: The Breach That Hid in the Code
A software error, a loan app, and Social Security numbers sitting exposed for 165 days. PayPal had a problem — and its customers were the last to know.
PayPal has disclosed a data breach that is, in many ways, more alarming than a headline-grabbing hack. There was no sophisticated adversary. No nation-state exploit. No dark web auction. Just a software bug in a loan application that quietly exposed the sensitive personal information of small business customers for nearly six months before anyone noticed.
The affected product is PayPal Working Capital (PPWC) — a financing tool designed to give small businesses fast access to cash. The window of exposure: July 1 to December 13, 2025. PayPal discovered the issue on December 12th and reversed the faulty code change the following day. The data left in the wind: names, email addresses, phone numbers, business addresses, Social Security numbers, and dates of birth.
For the people affected, that is essentially the full identity theft starter pack.
The Anatomy of the Exposure
This wasn’t a smash-and-grab. It was a door left quietly ajar.
The Root Cause: An error introduced through a code change made the PII of a “small number” of PPWC customers visible to unauthorized parties.
The Duration: 165 days. Five and a half months of exposure before PayPal’s own systems flagged it.
The Damage: PayPal confirmed unauthorized transactions occurred on a subset of affected accounts as a direct result of the incident and has issued refunds to those customers.
The Response: The faulty code was rolled back within 24 hours of discovery. Affected users are being offered two years of free three-bureau credit monitoring and identity restoration services through Equifax, with enrollment required by June 30, 2026.
PayPal stated it has not delayed notification due to a law enforcement investigation — which is notable, suggesting no criminal referral is currently in play.
This Is Not PayPal’s First Rodeo
Context matters here. This breach doesn’t exist in a vacuum.
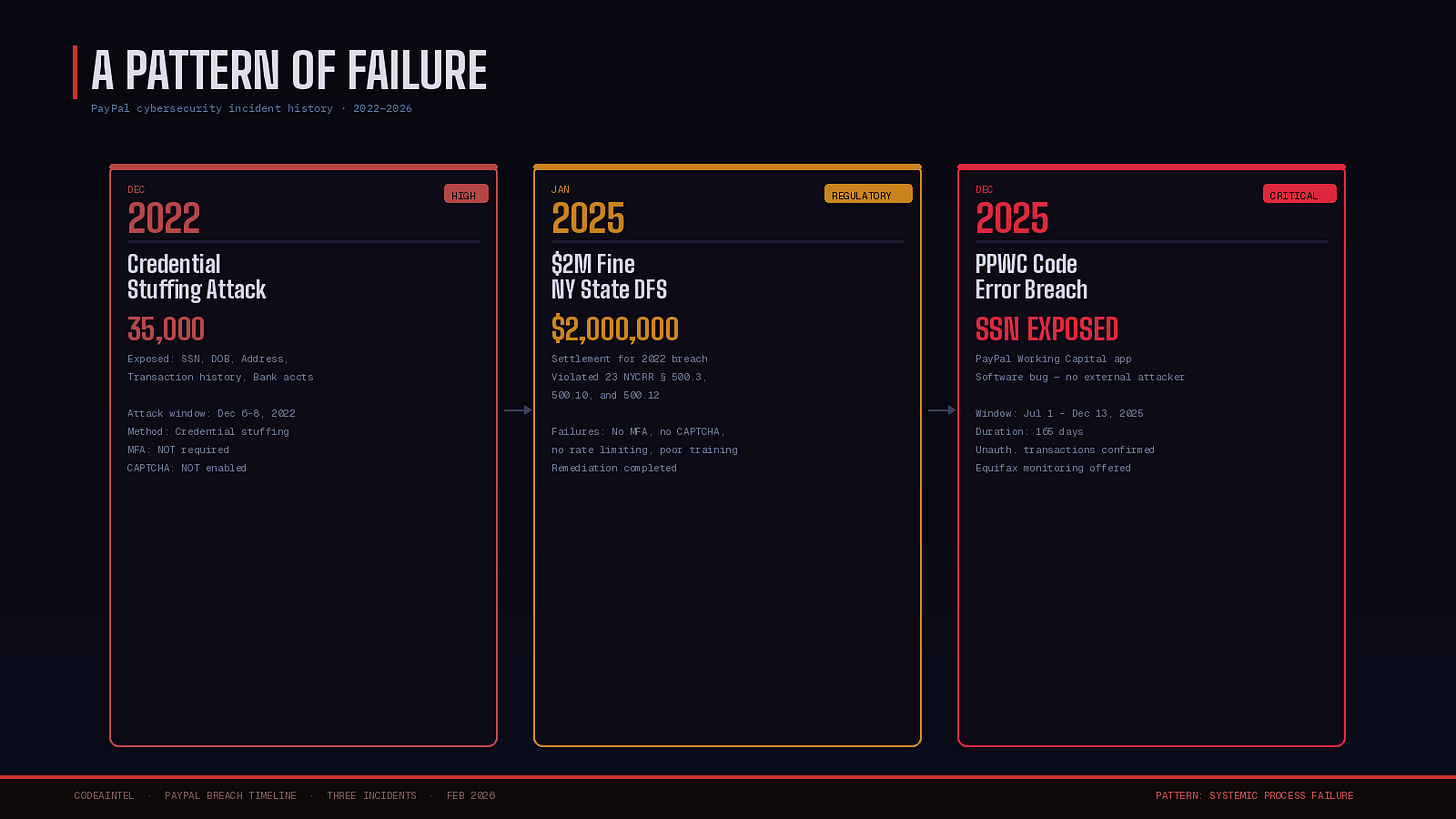
In December 2022, PayPal suffered a large-scale credential stuffing attack exposing roughly 35,000 accounts — including Social Security numbers and tax identification data. That incident eventually cost the company a $2 million settlement with the New York State Department of Financial Services in January 2025 for failing to comply with cybersecurity regulations. The DFS found that PayPal lacked proper CAPTCHA protections, rate limiting, and mandatory multi-factor authentication at the time.
Now, less than a year after that settlement was announced, PayPal is back in breach territory — this time not from an external attacker exploiting weak controls, but from an internal code change that bypassed its own data protection framework.
The pattern is hard to ignore: PayPal keeps putting sensitive data at risk through process failures, not just external threats.
What Small Business Owners Need to Do Now
If you use or have used PayPal Working Capital, treat this as a confirmed identity risk:
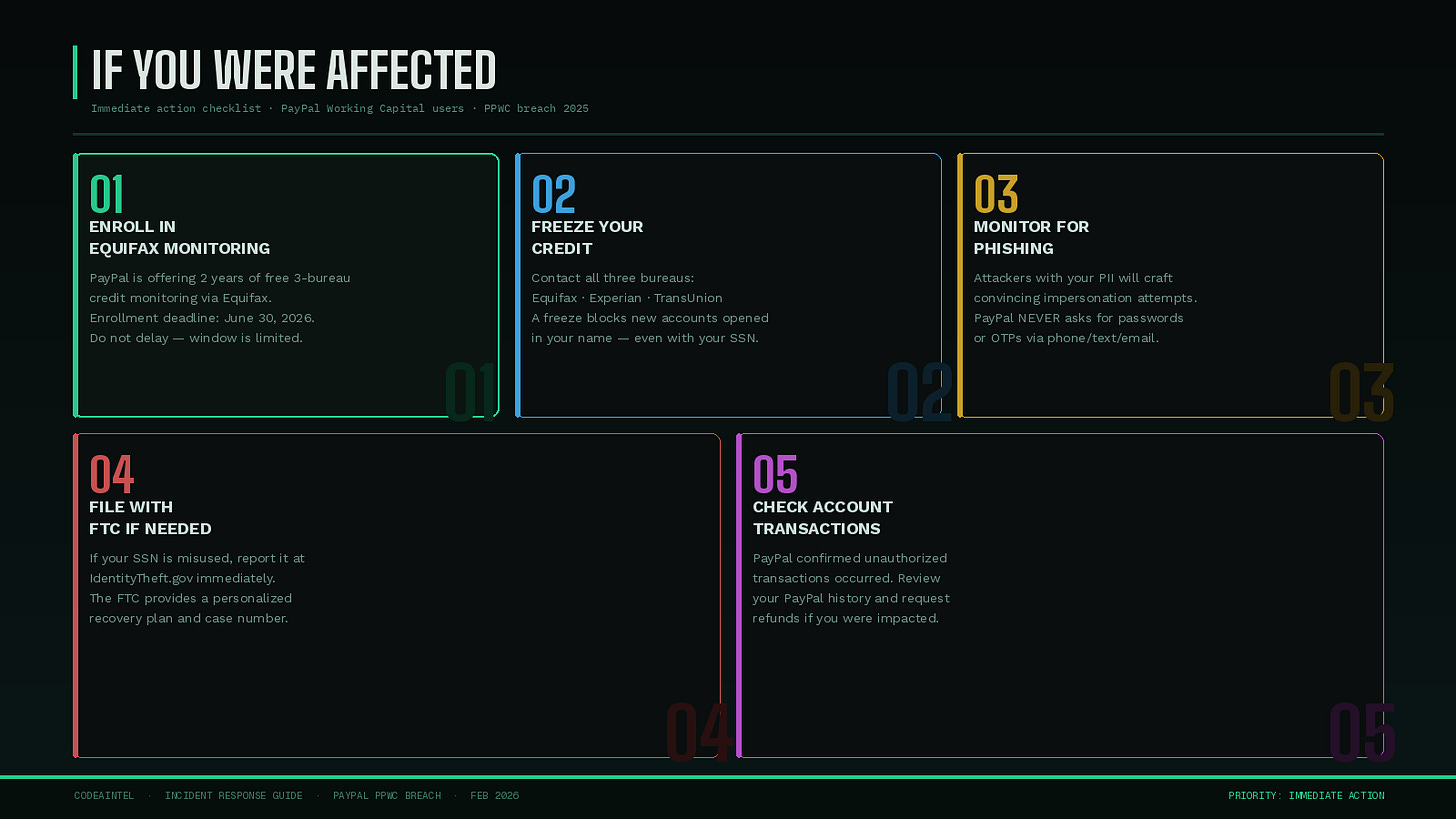
Enroll immediately in the Equifax credit monitoring offer PayPal is providing. Do not wait.
Place a fraud alert or credit freeze with all three bureaus (Equifax, Experian, TransUnion) if you want to go further.
Monitor your business and personal accounts for unauthorized transactions — PayPal has already confirmed some accounts were fraudulently accessed.
Watch for follow-on phishing. Attackers who obtained this data now have everything they need to craft highly convincing impersonation attempts. PayPal will never ask for your password, one-time codes, or authentication credentials via phone, text, or email.
File with the FTC at IdentityTheft.gov if you believe your Social Security number has been misused.
CodeAIntel Insight: The 165-day exposure window is the real story here. Modern breach detection should catch anomalous data access in hours or days — not months. The fact that a code-level error in a loan application could silently expose Social Security numbers for five and a half months points to a deeper problem: insufficient data-access monitoring at the application layer. For enterprises, the lesson is not “don’t write buggy code” — that’s a given. The lesson is: if sensitive PII is being touched by any application, you need runtime visibility into who is accessing it, when, and whether that access pattern looks normal. PayPal didn’t have that. Do you?
Sources:
https://www.bleepingcomputer.com/news/security/paypal-discloses-data-breach-exposing-users-personal-information/
https://www.documentcloud.org/documents/27345193-paypal-february-2026-breach-notification/