ZeroDayRAT: The Nation-State Toolkit Now Available to the Highest (Telegram) Bidder
The barrier to entry for total mobile domination just hit zero.
A new mobile spyware platform, dubbed ZeroDayRAT, has emerged on Telegram, offering a suite of surveillance tools that were once the exclusive domain of elite nation-state signal intelligence (SIGINT) units. For a fee, any buyer can now gain full, real-time access to a target’s digital and physical life through a self-hosted browser panel.
It’s not just a data stealer. It’s a total takeover of the person behind the screen.
The “Everywhere” Exploit: Android 5 to iOS 26
The technical reach of ZeroDayRAT is staggeringly broad. While many RATs (Remote Access Trojans) struggle with version updates, ZeroDayRAT is built for longevity:
Android: Supports version 5 all the way through the upcoming Android 16.
iOS: Supports versions up to iOS 26, leveraging enterprise provisioning profiles to bypass the App Store’s “Walled Garden.”
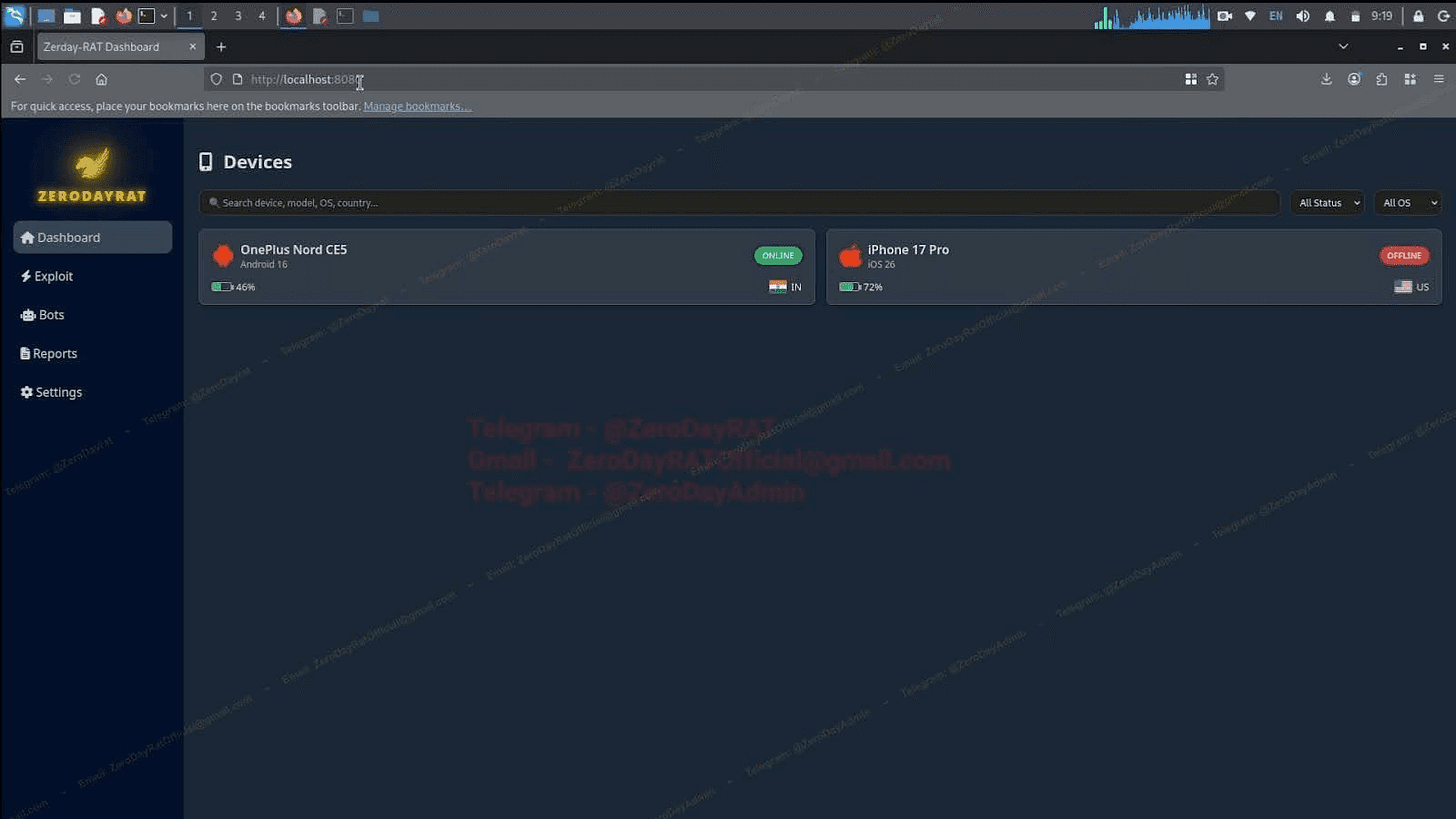
Distributed via social engineering and malicious “updates” on Telegram and fake marketplaces, the malware generates a custom binary for each target. Once installed, the attacker doesn’t just see files—they see a live dashboard of the victim’s existence.
The Real-Time Panopticon
ZeroDayRAT transforms a smartphone into a 24/7 surveillance beacon. The command-and-control (C2) panel provides:
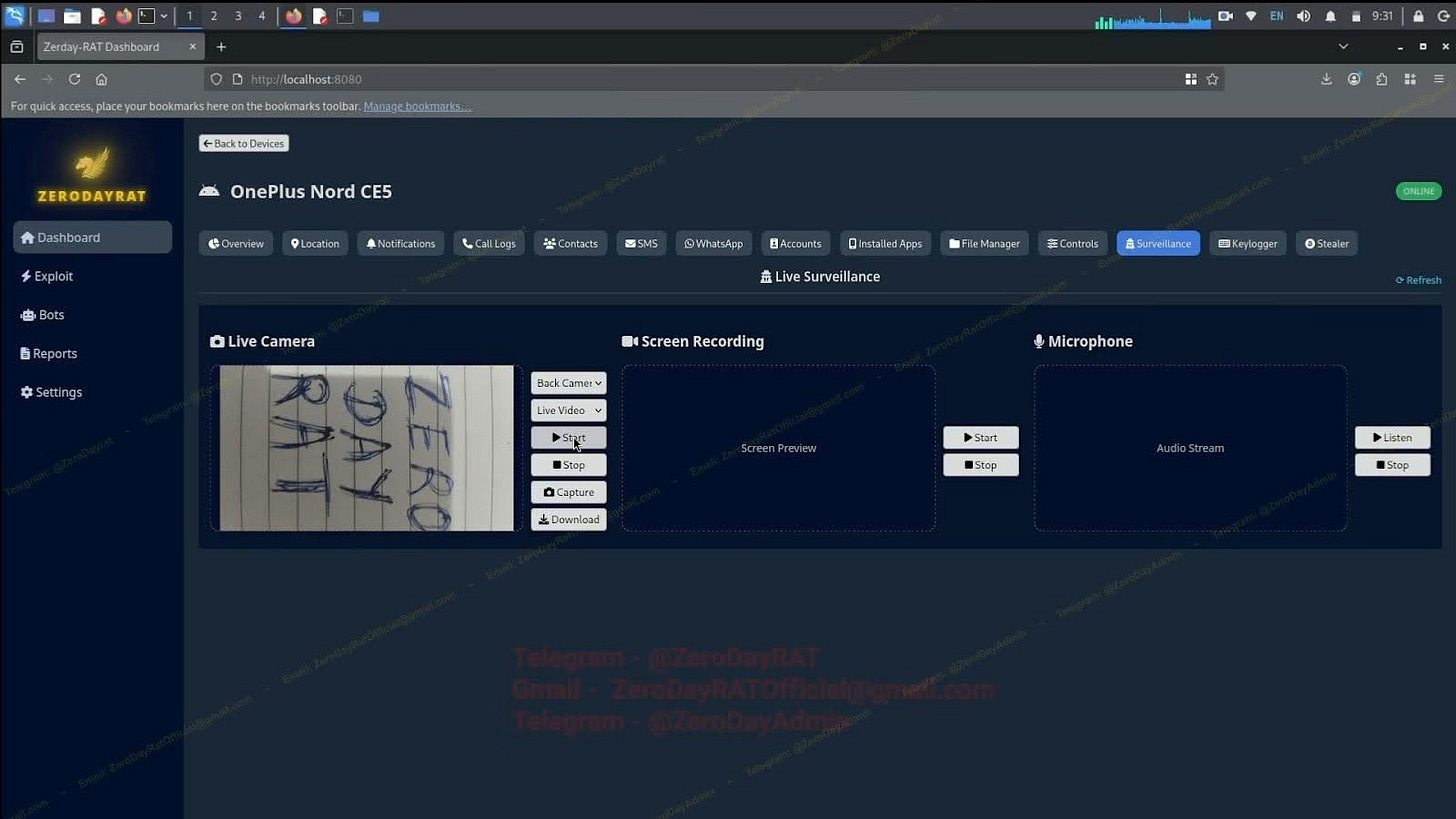
Live Eyes and Ears: Remote activation of camera streaming and microphone feeds.
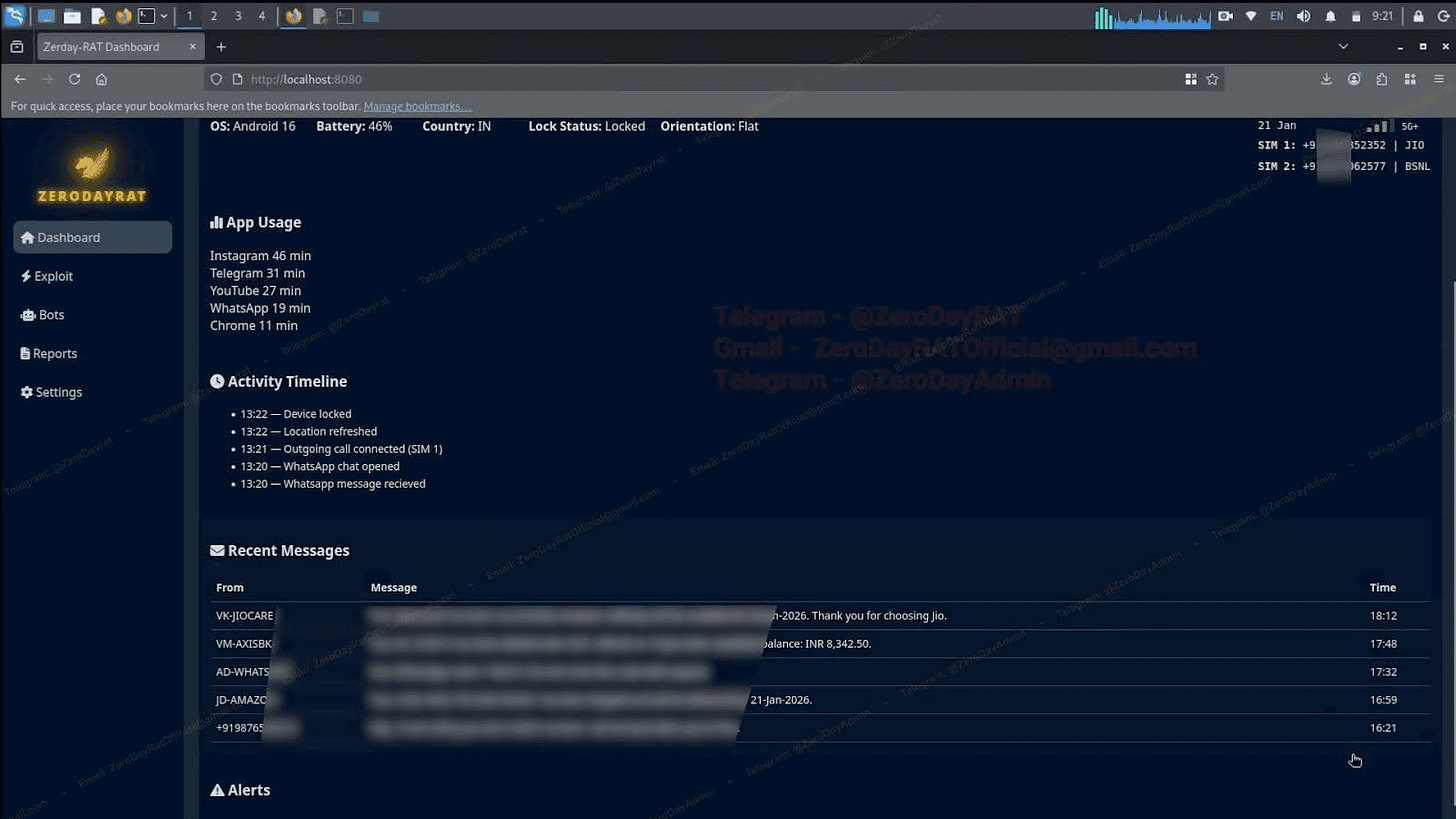
GPS Stalking: Real-time location plotting on Google Maps with a full historical breadcrumb trail.
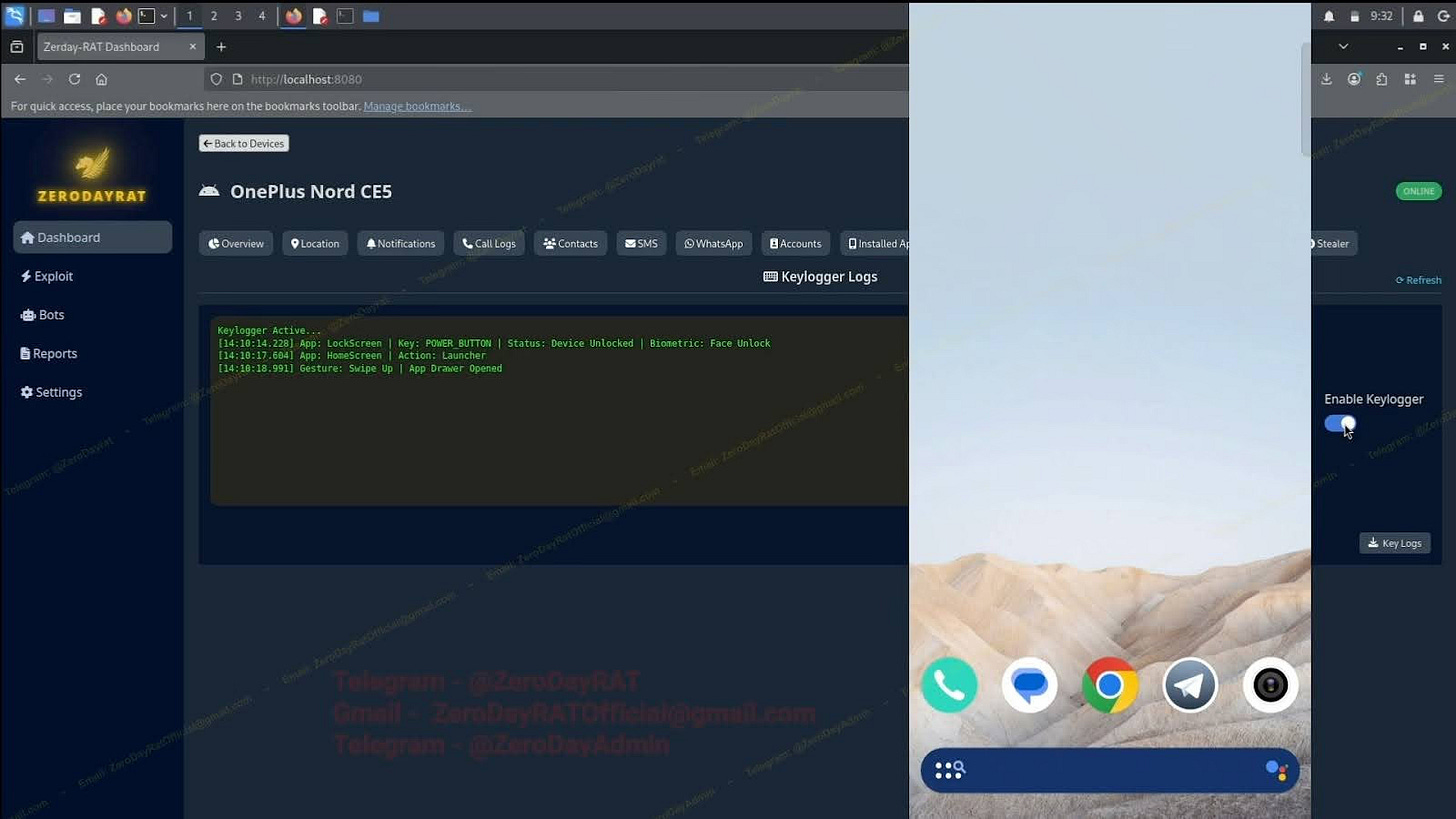
Keystroke Logging: Every password, message, and search query is recorded before it’s even sent.
Identity Mapping: The “Accounts Tab” enumerates every registered service—WhatsApp, Google, Facebook, Amazon, and banking apps—linking the device to the victim’s entire digital footprint.
Financial Warfare: Bypassing 2FA and Draining Wallets
ZeroDayRAT isn’t content with just watching; it’s designed to loot. The toolkit includes a sophisticated Bank Stealer and Crypto-Wallet Hijacker.
OTP Interception: By monitoring SMS in real-time, the malware intercepts One-Time Passwords (OTPs), effectively neutralizing Two-Factor Authentication (2FA).
Clipboard Substitution: The malware scans for wallet apps like MetaMask and Binance. When a user copies a crypto address, the RAT replaces it with the attacker’s address in the clipboard.
Payment App Takeover: It targets mobile payment ecosystems like Apple Pay, Google Pay, PayPal, and regional giants like India’s PhonePe (UPI).
The emergence of ZeroDayRAT represents a dangerous shift in the threat landscape.
Why this matters:
The Zero-Trust Necessity: If you are not verifying the origin of every “update” or “enterprise profile,” you are inviting an adversary into your pocket.
Biometrics vs. Keystrokes: While biometrics (FaceID/TouchID) are secure, the RAT logs the interaction after the vault is open.
The Telegram Shadow Market: The transition of these tools from private “zero-day” exploits to Telegram-accessible subscription models means the number of potential attackers has increased by an order of magnitude.
Source: https://iverify.io/blog/breaking-down-zerodayrat---new-spyware-targeting-android-and-ios